In today’s interconnected world, cybersecurity threats are more prevalent and sophisticated than ever before. Organizations of all sizes, from small businesses to multinational corporations, face a constant barrage of potential vulnerabilities. Effectively managing these risks requires a proactive and systematic approach, and that’s where security risk assessment software comes in. This comprehensive guide will delve into the intricacies of this critical technology, exploring its features, benefits, and considerations for successful implementation.
Understanding Security Risk Assessment Software
Security risk assessment software automates and streamlines the process of identifying, analyzing, and prioritizing security risks within an organization’s IT infrastructure and systems. It goes beyond simple vulnerability scanning, providing a holistic view of potential threats, their likelihood, and their potential impact. This allows organizations to make informed decisions about resource allocation and mitigation strategies.
Key Features of Security Risk Assessment Software
- Vulnerability Scanning: Identifies known weaknesses in software, hardware, and configurations.
- Threat Modeling: Analyzes potential attack vectors and their potential consequences.
- Risk Scoring and Prioritization: Assigns risk scores based on likelihood and impact, allowing for focused remediation efforts.
- Compliance Management: Helps organizations meet regulatory requirements (e.g., GDPR, HIPAA, PCI DSS).
- Reporting and Documentation: Generates comprehensive reports detailing identified risks, remediation steps, and overall security posture.
- Integration with other Security Tools: Seamlessly integrates with other security tools like SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) systems.
- Asset Discovery and Inventory: Automatically identifies and catalogs all IT assets within the organization’s network.
- Data Loss Prevention (DLP) Capabilities: Some advanced solutions include DLP features to identify and prevent sensitive data breaches.
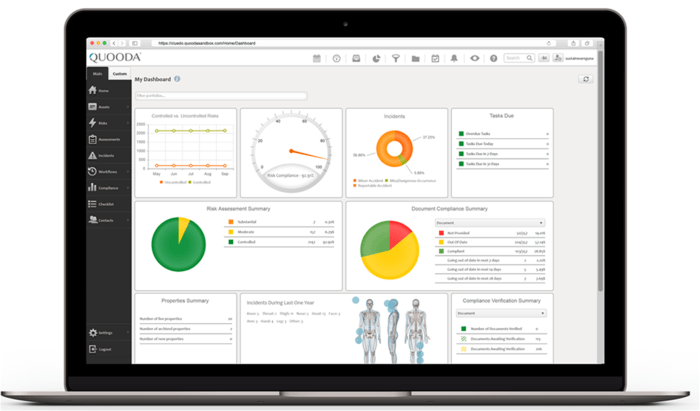
Benefits of Implementing Security Risk Assessment Software
Implementing robust security risk assessment software offers numerous benefits, including:
Source: hseorganiser.com
- Proactive Risk Management: Identify vulnerabilities before they can be exploited by attackers.
- Improved Security Posture: Strengthen overall security by prioritizing and addressing critical risks.
- Reduced Costs: Prevent costly data breaches and security incidents.
- Enhanced Compliance: Meet regulatory requirements and avoid penalties.
- Better Resource Allocation: Focus resources on the most critical risks.
- Streamlined Processes: Automate time-consuming manual tasks.
- Improved Decision-Making: Data-driven insights for informed security decisions.
- Increased Transparency: Provides a clear picture of the organization’s security posture to stakeholders.
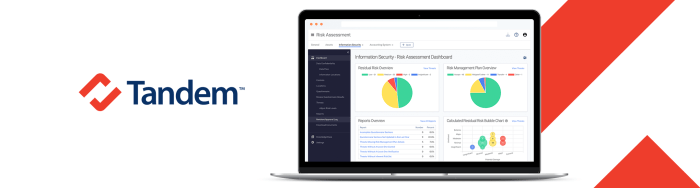
Choosing the Right Security Risk Assessment Software
Selecting the appropriate software depends on various factors, including:
Source: conetrix.com
- Organization Size and Complexity: Larger organizations with complex IT infrastructures require more sophisticated solutions.
- Budget: Software options range from affordable to enterprise-grade solutions.
- Specific Security Needs: Consider the specific types of risks the organization faces.
- Integration Capabilities: Ensure compatibility with existing security tools.
- Ease of Use: Choose software with a user-friendly interface and intuitive reporting features.
- Vendor Support: Select a vendor with a strong track record and responsive support team.
Types of Security Risk Assessment Software
Security risk assessment software comes in various forms, each catering to specific needs:
1. Cloud-Based Solutions
Offer scalability, accessibility, and ease of deployment. Ideal for organizations with geographically dispersed teams.
2. On-Premise Solutions
Provide greater control and customization but require dedicated hardware and IT resources.
3. Hybrid Solutions
Combine the benefits of both cloud and on-premise deployments, offering flexibility and control.
Security Risk Assessment Methodology
Most security risk assessment software employs a structured methodology, often incorporating elements of frameworks like NIST Cybersecurity Framework, ISO 27005, or OWASP.
Key Steps Typically Involved:
- Asset Identification: Identify all critical assets and systems.
- Threat Identification: Determine potential threats and vulnerabilities.
- Vulnerability Assessment: Scan for and identify existing vulnerabilities.
- Risk Analysis: Assess the likelihood and impact of each identified risk.
- Risk Prioritization: Rank risks based on their severity.
- Risk Mitigation: Develop and implement strategies to reduce or eliminate risks.
- Monitoring and Reporting: Continuously monitor and report on the organization’s security posture.
Frequently Asked Questions (FAQ): Security Risk Assessment Software
- Q: What is the difference between vulnerability scanning and security risk assessment?
A: Vulnerability scanning identifies weaknesses in systems, while security risk assessment analyzes the potential impact of those weaknesses and prioritizes remediation efforts. - Q: How often should I conduct security risk assessments?
A: The frequency depends on the organization’s risk profile and regulatory requirements, but regular assessments (e.g., annually or semi-annually) are recommended. - Q: What are the key metrics to track in security risk assessment?
A: Key metrics include the number of identified vulnerabilities, risk scores, remediation timelines, and overall security posture improvements. - Q: How can I ensure the accuracy of my security risk assessments?
A: Use reputable software, regularly update your vulnerability databases, and involve experienced security professionals in the process. - Q: What is the role of human expertise in security risk assessment?
A: While software automates many tasks, human expertise is crucial for interpreting results, making informed decisions, and developing effective mitigation strategies.
References
- National Institute of Standards and Technology (NIST)
- International Organization for Standardization (ISO)
- Open Web Application Security Project (OWASP)
Conclusion
Security risk assessment software is an indispensable tool for organizations seeking to proactively manage their cybersecurity risks. By automating the assessment process, prioritizing vulnerabilities, and providing valuable insights, this technology empowers organizations to make informed decisions, strengthen their security posture, and protect their valuable assets. Investing in the right software and implementing a robust risk management program is crucial for navigating the ever-evolving landscape of cyber threats.
Call to Action
Ready to elevate your organization’s cybersecurity posture? Explore the leading security risk assessment software solutions available today and take the first step towards a more secure future. Contact us to learn more about how we can help you find the perfect solution for your specific needs.
Clarifying Questions
What types of organizations benefit most from security risk assessment software?
Organizations of all sizes and across various industries can benefit. However, those handling sensitive data (healthcare, finance, etc.) or facing significant regulatory compliance requirements see the most significant advantages.
Source: rocketcdn.me
How much does security risk assessment software typically cost?
Effective security risk assessment software is crucial for any organization. Choosing the right developers to build or integrate such software is paramount, and that’s where finding one of the best nearshore software development companies becomes key. Their expertise ensures the software not only functions correctly but also adheres to the highest security standards, minimizing vulnerabilities and maximizing protection.
Pricing varies widely depending on the features, scalability, and vendor. Expect a range from subscription-based models for smaller businesses to enterprise-level solutions with higher upfront costs.
What are the key features to look for when selecting security risk assessment software?
Essential features include vulnerability scanning, risk scoring and prioritization, reporting and dashboards, integration with other security tools, and regular updates to address emerging threats.
How often should a security risk assessment be conducted?
The frequency depends on the organization’s risk profile and regulatory requirements. However, regular assessments (at least annually, and more frequently for high-risk environments) are recommended.
